
Today the European Agency for Cybersecurity (ENISA) released a robust report that details a disconcerting 58 viable threats and attack vectors within the 5G network infrastructure currently being rolled out across Europe.
The comprehensive aggregation of the threat landscape for 5G networks covers everything from core network vulnerabilities to virtualisation threats. The report also notes that protecting personal data is set to get tougher the further 5G reaches: “Growing concerns over availability and protection of user data and privacy will exacerbate with the security challenges introduced 5G.”
The report comes just a month after the European Commission issued an EU-wide warning and risk assessment relating to 5G security threats. (Today’s report will be followed by a “5G toolbox”, produced by the NIS Cooperation group and EU member states with ENISA support.)
In last month’s report the EU warned that 5G possess “a major security challenge” and a “new security paradigm”. The ENISA report, published today, adds a more detailed breakdown of the risks.
(The EU estimates there will be 1.5 billion 5G users by 2024.
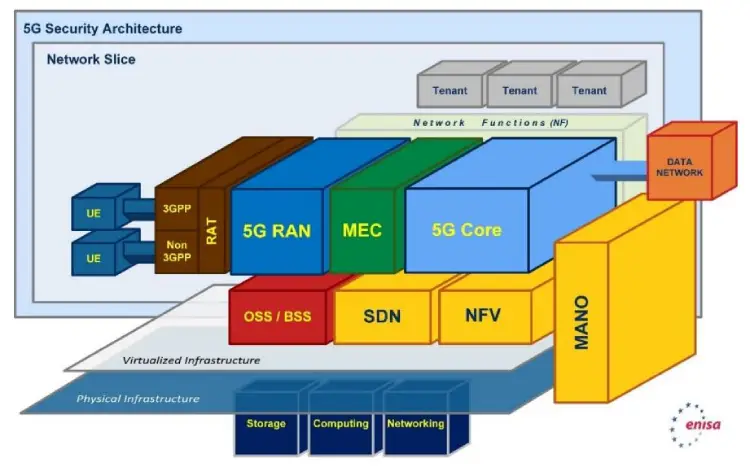
Core 5G Security Threats
A key concern is that bad actors will abuse the 5G network architecture’s heavy reliance on application programming interfaces (APIs).
ENISA is warning that even one small compromise of an API in the 5G core can put the whole network at risk.
“It is important to highlight that 5G infrastructure will rely on COTS solutions that extensively use open source APIs…The exploitation can target different types of API naming internal network functions, internet working interfaces, roaming interfaces, etc. exposed in different layers of the network.”
The manipulation of network configuration data by threat actors is a huge issue that could affect the security and integrity of the network. In this scenario hackers would compromise a network component such as a SDN controller, orchestration or network function in order to reshape configuration data so they can launch more critical attacks.
ENISA notes that: “Inadequate policies in the management and protection of critical configuration data may lead to unpredictable system behaviour and unauthorised access to critical platforms, with impact on the confidentiality and integrity of the network.”
Other core network threats detailed by ENISA include the malicious diversion of traffic, side-channel attacks, memory scraping and the abuse of lawful interception function. The latter in that list involves a hacker intercepting information in the network that belongs to a law enforcement monitoring facility, so needless to say these aren’t inconsequential threats.
Edge gateways
Edge gateways which process and transmit data from edge devices are open by nature and will see increasing use with the establishment of 5G networks. However, they will also possess a significant risk to the network as threat actors will be able to deploy their own gateway devices that can be used to initiate attacks in the same manner that web based man-in-the middle attacks play out today, ENISA also fears.
Virtualisation Threats
Attackers could potentially target and abuse the interconnected (DCI) protocols that are used by datacentres and are instrument in the operation of virtualised systems. ENISA notes that through the “Exploitation of specific vulnerabilities of Data Centers Interconnect (DCI) protocols (e.g. lack of authentication and encryption). An attacker could create spoofed traffic in such a way that it traverses DCI links or to create a DoS attack of DCI connections.”
Recommendations to Mitigate 5G Network Threats
ENISA believes that all stakeholders in the network need to work together in a transparent manner if the threats to the 5G network are to be mitigated. It also recommends that vendors, operators and verticals have open discussions around the technical and organisational nature of the network.
The agency says closer cooperation, based on a close reading of its report, would speed up the adoption of security requirements and secure 5G practices and will create competitive advantages within the entire EU space.”






