
Security firm Onapsis says it has identified a series of critical vulnerabilities in Oracle’s E-Business Suite (EBS) that could allow attackers to gain “untraceable control” of electronic fund transfers and print bank checks without detection.
The attack chain exploits two key vulnerabilities, dubbed Oracle PAYDAY by the Boston-based cybersecurity firm. While Oracle has now patched the flaw, Onapsis says it estimates that half of Oracle’s ERP software customers have not deployed the patches: meaning over 10,000 companies are still at risk.
Many of these are only running the software on internal intranets, but Onapsis estimates that at least 1,500 EBS systems are connected directly to the internet. Without patching, the flaw can be exploited remotely by an unauthenticated attacker, who would gain complete access to the widely used ERP system.
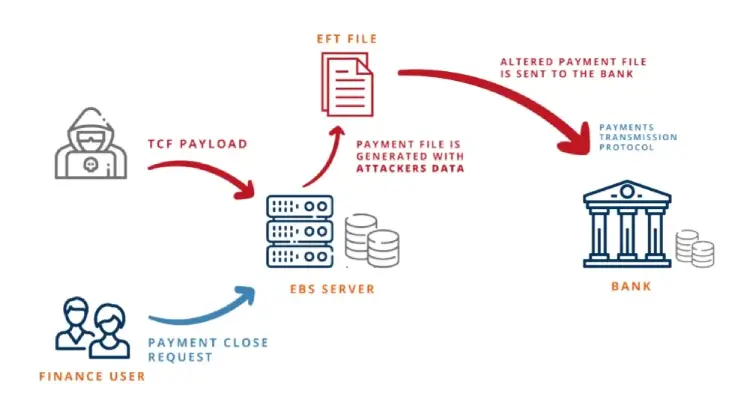
The vulnerabilities target a API in the E-Business Suite (EBS) product — the Thin Client Framework (TCF) API provided by Oracle, so developers can build server-based applications — and score a critical 9.9 out of 10 on the CVSS scale.
With Oracle EBS including a Payments module that allows
companies to actually transfer money from bank accounts or generate payment checks, malicious takeover could be hugely damaging for victims.
See also: Oracle Patches 219 Security Vulnerabilities – 142 Remotely Exploitable
The first Oracle Critical Patch Update (CPU) to fix the issue was released in April 2018 and subsequent patches have continued to fix different aspects of the flaw, including the last available fix for the critical vulnerabilities (CVE-2019-2638, CVE-2019-2633) in the April 2019 CPU, Onapsis said.
While the ERP includes auditing tables for Payment modules, as the SQL protocol allows attackers to execute arbitrary queries with APPS users, it is possible to disable and erase these audit log tables, Onapsis said; the company added that it successfully created a proof of concept that detects and erases
audit tables, using specially crafted queries.
“Finally, a set of database triggers are created to restore all the information as it was before the attack, leaving no trace or clue to what happened.”






