
A major provider of solid state drives (SSDs), SanDisk, was caught using unencrypted HTTP communications to send updates from its servers to end-user’s devices, and opting for a hard-coded password to protect system diagnostic reports, in a brace of security howlers disclosed today by cybersecurity company Trustwave.
The two vulnerabilities, allocated the CVEs 2019-13466 and 2019-13467 respectively, have now been patched, but point to still alarmingly common poor security practices by parent company Western Digital, which reported annual revenues of $20.6 billion in 2018. Trustwave researcher Ed Williams, who spotted the issues, described them to Computer Business Review as “seriously fundamental errors”.
See also: Security Researcher Alleges Assault by Casino Vendor for Vulnerability Disclosure
SanDisk sells consumer SSDs, with parent company Western Digital also furnishing data centres with HDDs, SSDs and memory extension drives. The vulnerabilities affected both the Western Digital and SanDisk SSD Dashboard applications; a management utility that handles software updates and customer report data.
Vulnerabilities Affected both Consumer SanDisk and Enterprise Western Digital Management Utility
Williams found the issue almost by chance, when installing the management utility on his own laptop after buying a new SSD. He said in a blog today: “A quick examination revealed a some potentially dangerous vulnerabilities in it.
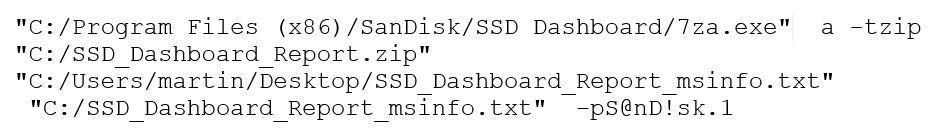
“I discovered the first vulnerability (CVE-2019-13466) when doing quick strings dump from the main application binary. [I found that] the app uses a hard-coded password to protect customer report data which is then supposed to be sent to SanDisk for examination. Needless to say, this “encryption” has no value.
“The second vulnerability (CVE-2019-13467 — ) is more severe. Using a network capture running on the same computer as the app, it was clear that the application uses HTTP instead of HTTPS for communication with SanDisk site. This makes it trivial to attack users running this application in untrusted environments (e.g. using public internet hotspot). Specifically, a malicious user can create a rogue hotspot that the computer will join or launch a man-in-the-middle attack and then serve malicious content.”
SanDisk/Western Digital’s patches mean HTTPs is now used, but when it comes to the hard-coded password, the company appears to have opted for the easiest option: stripping the feature out. Its advisory says: “The updated application will no longer encrypt the system information report files, and customers requiring support should instead directly share such reports with our Customer Support teams only.”
Bad Practice, but All Too Common
The issues suggest another case of the endemic industry issue of application developers under pressure to churn out code, with little security baked into the process.
Williams told Computer Business Review: “In their defence they responded fast, got through the issues and remediated pretty quickly. It was also easy to disclose to them.
“I suspect that this [the application features] was done a while ago and then just left there. It points to a lack of a Secure Development Lifecycle approach; it also looks like they’d benefit from some pentesting looped into their SDL. It’s really, really bad practice to use hard coded credentials, particularly when it is so easy to get automated scripts that will go through codebases looking for them…”

“All the tools that enable you to create secure processes are out there and fairly trivial to use. But too often software engineering and security just don’t meet; even at university, too often courses don’t bring them together. How, in 2019, are we still using HTTP?”
Western Digital did not respond to a request for comment.
The company reports its quarterly earnings today. Its investor relations page throws up a security warning: it defaults to an HTTP page…






