
Government security officials are planning crisis talks on May 8 over nascent plans by Google to implement an encrypted DNS offering and bundle it into the popular Chrome browser, the Sunday Times reports; a move that would make it significantly harder for the government to conduct bulk surveillance of the UK’s internet traffic.
While Google – to Computer Business Review’s knowledge – has not explicitly unveiled these plans yet, commits to the Chromium repo shows that Google is working to add support for it in a future update and others are moving fast to do the same.
Read this: FTSE 100 Vulnerability Warning: Over 70% Have Single DNS Provider
Encrypted DNS: Pilots Proliferating
Facebook, for example, has partnered with Cloudflare to offer DNS-over-TLS as a pilot project. As the company put it on December 21: “Online security has changed considerably since the late 1980s, when the Domain Name System was first standardized to allow connection to entities by the means of simple mnemonic names, such as facebook.com.”
“…DNS requests and answers are still sent in the clear. This leaves them easily read by any party in the path between the requestor and the responder.”
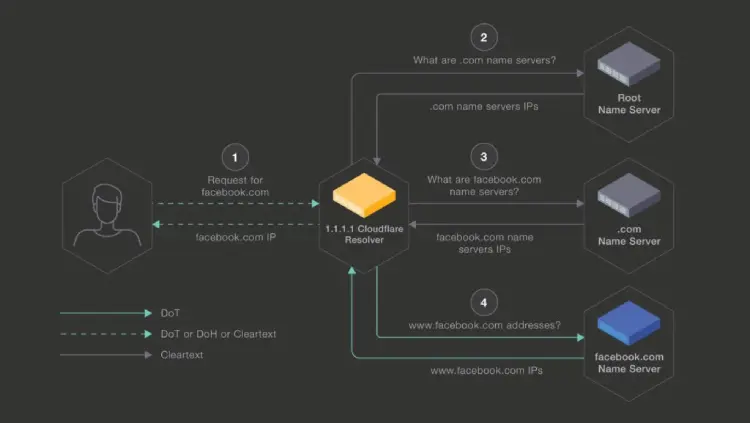
In an attempt to test encryption of all DNS queries it enabled DoT between Cloudflare’s 1.1.1.1 recursive resolvers and its own authoritative name servers during a pilot last year. The goal, Facebook said, “is to understand the feasibility of doing this at scale, gather metrics to better understand the overhead incurred in terms of latency on receiving an answer, and determine computing overhead. This pilot will allow us to better understand how the protocol behaves in the wild.”
Mozilla, meanwhile, is piloting the use of a DoH opt-in in its Firefox browser (again underpinned by Cloudflare’s service) saying “DoH and DoT deployments are both exciting steps toward providing greater security and privacy to all”.
Mozilla is seeking to “build a larger ecosystem of trusted DoH providers” with a renewed pilot starting this month.
UK Government, broadband ISPs and the National Cyber Security Centre (NCSC) will meet May 8 and are reportedly particularly concerned about the ability this could have to disrupt their future ambitions under the Online Harms White Paper, along with broader security, the the forthcoming porn age-check requirements and more.
Paul Gagliardi, Director of Threat Intelligence at SecurityScorecard said in an emailed comment: “This is a classic example of when increasing privacy can negate security controls. What was initially driven by the desire for ISPs or others monitoring my traffic to NOT know the websites I am visiting, has downstream consequences such as the inability for a school to block their students from visiting pornography sites. The tech/security community is somewhat divided on this. On one hand I don’t want ISPs selling my internet behavior or censoring it, on the other it is currently hard to implement basic censoring.”
“Ultimately, content (DNS in this case) cannot be secured/monitored without having the ability to observe it. Just as companies/organizations inspect their HTTPS traffic, the same needs to happen with encrypted DNS/DoH. Decrypting DoH would be the exact same mechanism as observing HTTPS traffic, using a Man in the Middle proxy to decrypt traffic on the fly and implement security mechanisms. There are no shortage of commercial solutions for this, however, things get more complicated in “Bring Your Own Device” environments.”
He added: “DoH forces the privacy vs security defense debate to be more localized. A company or organization can balance those decisions in their network differently than a private individual. Unfortunately for those organizations/companies, the ability to censor traffic is now more technical and requires more investment on their part. In short I think we’ll see more HTTPS MiTM and prohibition of BYoD.”






