
A report by analytics software provider SAS warned today that the UK is a procurement fraud “capital” – with almost a third (31 percent) of businesses subjected to contract bid rigging and 43 per cent to duplicate invoices.
The damages can be great: 40 percent of UK companies hit by procurement fraud lose between €150,000 and €400,000 a year, SAS claimed. Other types of procurement fraud include ghost vendors and payroll fraud.
“British companies take a relaxed attitude to auditing and have largely failed to make the most of new technologies in the fight against fraud” SAS said today, adding that British businesses (29 percent) also notably lag their EMEA counterparts (46 percent) when it comes to holding regular audits into procurement fraud.
The company’s report is frank about the reasons for lack of adoption: “Detection software tends to be more objective [than manual interventions], but the implementation is usually rudimentary and rules-based.”
“The technology casts a very wide net, meaning innocent accidents or anomalies are flagged alongside genuine signs of fraud. False positives such as these waste time and resources while real fraud continues in the background.”
SAS is promoting Machine Learning-based approaches instead.
Read this: What is this Mystery Company Doing Procuring £1 BILLION of IT Equipment?
While the sample size of 850 business leaders is comparatively small, other research supports SAS’s findings: PwC’s 2018 Global Economic Crime survey found procurement fraud to be the third most widely reported economic crime in the UK – the company said it has seen a 28 percent rise in recent years, dubbing it a “significant hidden cost, particularly in high-volume, lower-margin businesses.”
PwC’s report found that 19 percent of frauds were detected through fraud risk management and 15 percent were detected by internal audit. The success of suspicious transaction monitoring (from 22 percent in 2016 to 10 percent in 2018) and data analytics (8 percent to 1 percent) has declined in the UK.
Procurement Fraud: Not Enough Technical Intervention
“These figures are only the tip of the iceberg’ said Laurent Colombant, Continuous Compliance and Fraud Manager at SAS.
“Procurement fraud is notoriously difficult to detect and measure. This is due to a lack of preparedness and awareness, as well as its bugbear status, among businesses. As a result, the true scale of the challenge is almost certainly underestimated.”
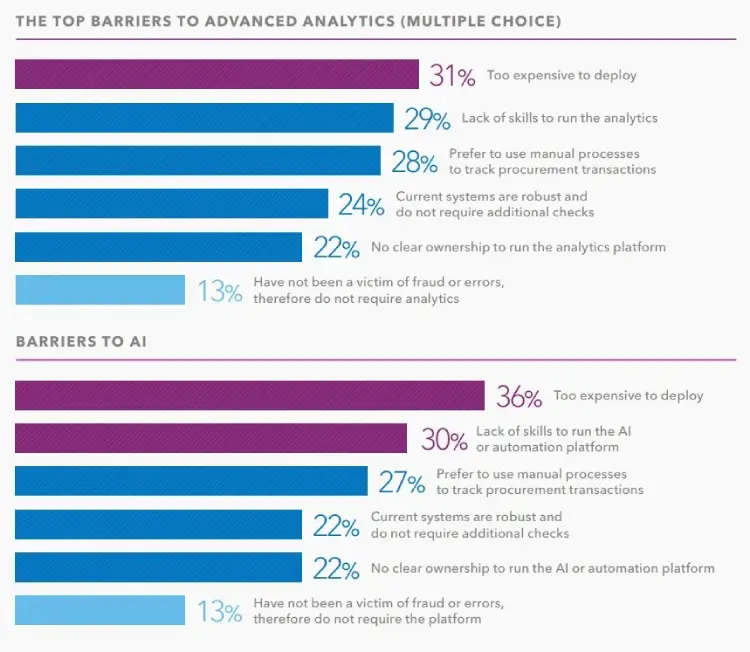
Only 12 percent of British companies use advanced analytics technologies to combat procurement fraud, meanwhile and only 9 percent have adopted AI tech, SAS said.
“UK companies are far more likely to process procurement applications manually and depend on staff to report wrongdoing against EMEA averages.”
The country’s most common detection techniques include manual controls (43 percent), rules-based software detection (38 percent) and anomaly detection (32 percent).
Resistance to software tools to detect fraud should soften, SAS urged.
The return on investment (ROI) can be adequately measured, the technology has improved immeasurably and analytics-enabled modes of detection are much faster than manual controls. (The median duration of internal procurement fraud is 16 months, but the length can vary considerably depending on its type. Payroll fraud for example can continue for as long as 30 months.)
“Machine learning models also have the added advantage that they learn over time, meaning they can detect new threats and techniques as they emerge. This is distinct from manual controls and rules-based detection, which take a rear-view mirror approach — analysing old data and patterns retrospectively as opposed to real-time reviews” the company said.






