
Microsoft has open sourced a UEFI codebase that is the basis for the system firmware within a number of Microsoft’s own products.
UEFI (Unified Extensible Firmware Interface) firmware initialises PCs when they are powered on, including the security foundation.
The codebase, dubbed Project Mu, demonstrates a way of building UEFI that streamlines security updates and reduces time to market for new features.
The “full-featured, product-ready UEFI firmware codebase” combines code from a multitude of sources, including silicon vendors.
Microsoft open source UEFI project with lots of cool security features and a reduced attack surface. Hope to see OEMs pick this up and more community PRs https://t.co/n2Sexc5LJK
— Dave dwizzzle Weston (@dwizzzleMSFT) October 15, 2018
These include TianoCore (itself an open source implementation of UEFI) EDK2 UEFI standard-based code; value-add code from TianoCore; silicon vendor hardware initialisation code; silicon vendor value-add code; independent BIOS Vendor code, board-specific code and more.
See also: Microsoft Demands “Digital Peace” – What Does It Really Want?
A Microsoft spokesman told Computer Business Review: “Project Mu improves security by removing unnecessary legacy code (a security practice known as attack surface reduction) and by enabling the newest UEFI security mitigations.”
They added: “Microsoft products, such as Surface, leverage Project Mu to quickly deliver industry-leading security features and patches to its customers.”
UEFI Security Concerns Rise Following Malware Discovery
The release comes three weeks after cybersecurity vendor ESET identified the first UEFI malware discovered “in the wild”.
Bratislava, Slovakia-based ESET, a threat detection specialist, late last month described the discovery [pdf] of malware dubbed “Lojax” that used repurposed commercial software to create a backdoor in computers’ firmware.
The rootkit has been active since at least early 2017 and is capable of surviving the re-installation of the Windows operating system or even hard drive replacement, ESET said.
The company’s research was the first to show that the previously identified malware was actively attacking the firmware of computers.
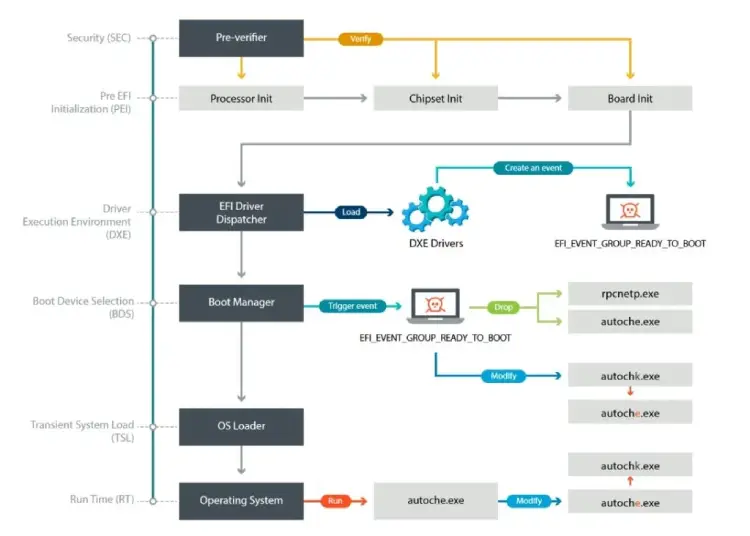
The finding threw the spotlight on a previously niche area of security, but came as concerns heightened about UEFI’s potential as a hiding place for rootkits.
As Dick Wilkins and Jim Mortensen of firmware developer Phoenix Technologies put it in a presentation at UEFI Plugfest last year (h/t Arstechnica) “Firmware is software and is therefore vulnerable to the same threats that typically target software.”
Microsoft said in a Q&A on Github: “We hope that Project Mu serves as a concrete example for discussing different approaches to managing the challenges faced by the UEFI ecosystem. It represents a variant of TianoCore that was customized within Microsoft for scaling and maintainability.”
The company added: “It’s not exactly a staging branch for TianoCore, as there are some changes that may not have application within or meet the explicit goals of that project, but it is a place where features and changes can be publicly featured and discussed.”
Project Mu can be found on GitHub.






