
The leader of the LockBit ransomware group has been revealed as Dmitry Khoroshev. A Russian national, Khoroshev’s identity as the mastermind behind the ransomware group was revealed in joint statements by the UK’s National Crime Agency and the US Department of Justice (DoJ). Known to most cybersecurity researchers as ‘LockBitSupp,’ Khoroshev is now subject to a US indictment, with the DoJ offering up to $10m for information that may lead to his arrest and conviction. The alleged cybercriminal is also being sanctioned by the US, UK and Australia.
“These sanctions are hugely significant and show that there is no hiding place for cybercriminals like Dmitry Khoroshev, who wreak havoc across the globe,” said the NCA’s director-general, Graeme Biggar. “Today’s announcement puts another huge nail in the LockBit coffin.”
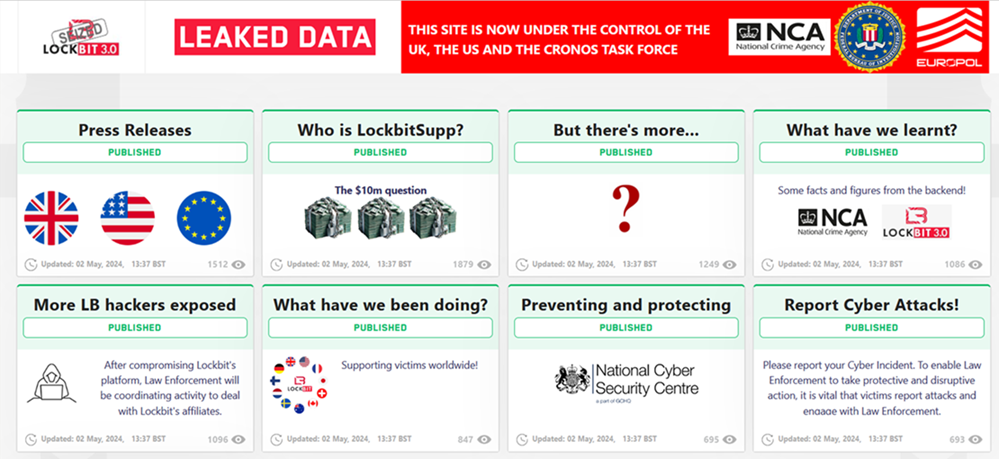
LockBit website used to reveal its leader’s hidden identity
According to the DoJ, Khoroshev is 31 and a resident of Voronezh, a small city in southwestern Russia. He has been charged with 25 counts of fraud, extortion, conspiracy to commit wire fraud and intention to cause damage to a protected computer, among other crimes. Operating LockBit according to a ransomware-as-a-service model, Khoroshev demanded a 20% cut of any ransom payment received as a result of using LockBit ransomware, a formula that the DoJ estimate netted the alleged cybercriminal a personal fortune of over $100m.
Khoroshev’s identity was revealed as part of a joint effort by the NCA, FBI and other international partners to infiltrate and dismantle LockBit. Known as ‘Operation Cronos,’ the action led to the seizure of LockBit’s victim blog and, the NCA claims, a 73% reduction in the number of monthly attacks by the group against targets in the UK. However, the joint action did not completely succeed in disabling the gang, with the infamous LockBitSupp opining on a new .onion site that the organisation remained operational.
Operation Cronos also led to an unprecedented intelligence haul on the gang’s inner workings and reach. In total, 194 affiliates were identified as having used the gang’s services. Of these, said the NCA, 148 built attacks and 119 engaged with victims over possible ransoms for their data, with deletion after the extortion process was completed far from routine. As a result of Operation Cronos, however, the NCA and its partners claim to have 2,500 decryption keys for victims of LockBit ransomware, with the former agency reaching out to some 240 victims in the UK.
Ransomware gang’s victims spread far and wide
Discovered by cybersecurity researchers in 2019, LockBit ransomware has been used in many high-profile breaches in recent years, with victims in the UK including the Post Office, the NHS and the Ministry of Defence. “The true impact of LockBit’s criminality was previously unknown, but data obtained from their systems showed that more than 7,000 attacks were built using their services between June 2022 and February 2024,” said Europol in a separate statement, with the top five countries hit being the UK, the US, France, Germany and China.
Searchlight Cyber’s head of threat intelligence, Luke Donovan, praised law enforcement agencies for targeting Lockbit and choosing to publicly undermine the organisation’s reputation for criminal competence on its own website. This, said Donovan, “demonstrates a new playbook that other law enforcement task forces could emulate to make life difficult for ransomware groups and other cybercrime gangs.”
Donovan warned, however, that LockBit was just one of several ransomware big beasts lurking on the dark web. “Any gap left by it will likely be filled by one or several of its competitors,” he said. “However, there is no doubt that this operation has been a major win for law enforcement, effectively exposing and disrupting one of the major culprits.”






