
Symantec researchers have uncovered a new Trojan named FASTcash which is been used by threat actors to make withdrawals from ATM’s across the world.
A U.S government alert estimates that the group known as Lazarus (U.S code name ‘Hidden Cobra’) has stolen tens of millions of dollars across 30 different countries.
The U.S alert found that in one incident in 2018, “HIDDEN COBRA actors enabled cash to be simultaneously withdrawn from ATM’s in 23 different countries.”
The Lazarus group infected banking networks with the Trojan FASTcash. They injected a malicious Advanced Interactive eXecutive (AIX) into the banks’ switch application server and into the legitimated process where the network handles ATM transactions.
The U.S government alert states that: “The IBM AIX executable files were designed to conduct code injection and inject a library into a currently running process. One of the sample AIX executables obtained provides export functions, which allows an application to perform transactions on financial systems using the ISO 8583 standard.”
It is this executable that Symantec has identified as malware.
The Trojan serves two purposes, first it scans all incoming messages to the system, such as withdrawal requests from an ATM. As the Trojan reads incoming network traffic it is looking out for primary account numbers (PAN) that have been flagged by the attackers for special treatment.
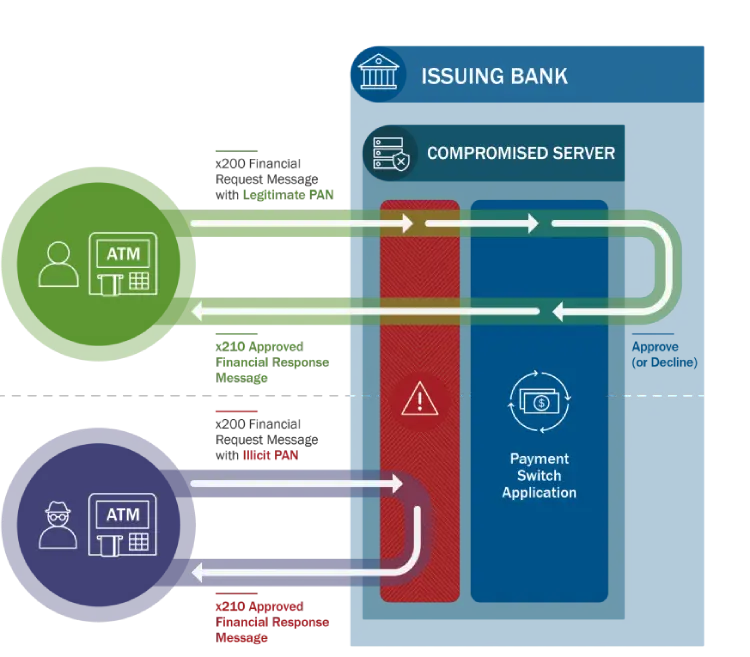
The malware constructs a fake response to the withdrawal request allowing the hackers to take out the requested money. This is done by making the compromised server send a fraudulent response back to a request, instead of it reaching the payment switch application.
Lazarus FastCash
U.S officials found the group: “Exploited the targeted systems by using their knowledge of International Standards Organization (ISO) 8583—the standard for financial transaction messaging…Actors most likely deployed ISO 8583 libraries on the targeted switch application servers.”
Symantec researchers have shown a sample of the response logic that the Trojan,FastCASH uses to create fake responses:
“This particular sample has logic to construct one of three fake responses based on the incoming attacker request:
For Message Type Indicator == 200 (ATM Transaction) and Point of Service Entry Mode starts with 90 (Magnetic Strip only):
If Processing Code starts with 3 (Balance Inquiry):
Response Code = 00 (Approved)
Otherwise, if the Primary Account Number is Blacklisted by Attackers:
Response Code = 55 (Invalid PIN)
All other Processing Codes (with non-blacklisted PANs):
Response Code = 00 (Approved)”
Symantec and U.S officials both note that the all of the compromised switch application severs were ruining on an outdated version of IBM Advanced interactive eXecutive (AIX) operating systems. U.S authorities say that they have found no evidence that the threat actors were exploiting the AIX OS in these attacks.
Lazarus
Lazarus are a highly active group of cyber criminals operating across the world. Investigators were first made aware of the group after the 2014 Sony Pictures hacking incident which saw a vast amount of personal data stolen from the company and resulted in many systems been replaced due to malware infection.
Symantec researchers have linked the group to the WannaCry ransomeware attacks citing that: “Three pieces of malware linked to Lazarus were discovered on the victim’s network: Trojan.Volgmer and two variants of Backdoor.Destover, the disk-wiping tool used in the Sony Pictures attacks.”
See Also: Hackers Earn Bitcoin through Fake Elon Musk Verified Accounts on Twitter
The Lazarus group would have needed to use other cybercrime techniques to carry out the Trojan.FASTcash attack. It is suspected that the compromise of the banking system was done through a spear-phishing campaign. However the initial infection vector used by the attackers is still unknown.






