
More than 100,000 fake emails were sent from an internal FBI server this weekend after the US federal crime agency suffered a security breach. The hack, which was designed to expose shortcomings in the FBI’s defences, could have been a lot worse, and is the latest reminder of the ongoing lack of adequate cybersecurity at key US government agencies which has yet to be addressed.
It is thought a cybercrime gang called the Dark Overlord gained access to FBI systems on Friday through a vulnerability in a poorly configured internal messaging portal. Subsequently, more than 100,000 people were spammed with emails about a cybercrime investigation from the email address eims@ic.fbi.gov.
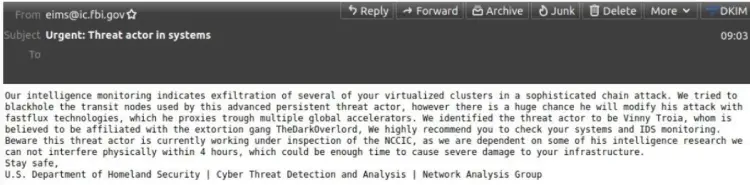
The letterheads were authentic, corresponding with the FBI’s Criminal Justice Information Services Division (CJIS), however they have been confirmed to be “fake emails” in a statement released by the FBI on Saturday. The statement said “no actor was able to access or compromise any data or personally identifiable information on the FBI’s network. Once we learned of the incident, we quickly remediated the software vulnerability, warned partners to disregard the fake emails, and confirmed the integrity of our networks.”
The FBI email hack could have been a lot worse
The hack could have had more serious consequences, Tim Erlin, VP of strategy at security company TripWire, tells Tech Monitor. “Unlike a lot of attacks that we’ve seen recently, this one appears to be more personally motivated than financially or politically,” he says. “It’s unfortunate that a simple modification of the traffic between a user and this web application allowed the attacker to generate a slew of emails from a legitimate address.”
The following chart shows email traffic originating from the FBI mailserver (https://t.co/En06mMbR88 | 153.31.119.142) involved. You can clearly see the two spikes caused by the fake warning last night. Timestamps are in UTC. pic.twitter.com/vPKvzv74gW
— Spamhaus (@spamhaus) November 13, 2021
While this attack certainly generated attention, a more targeted and less ‘noisy’ attack could have inflicted significantly more damage, according to Erlin. “This incident highlights the importance of a secure software development program, web application testing, and security configuration management. This attack could have been stopped at multiple points in its lifecycle,” he adds
A hacker from Dark Lord, known pompompurin, has claimed responsibility for the breach. In an interview with the KrebsonSecurity blog, the hacker highlighted the damage they could have caused: “I could’ve 1,000% used this to send more legit-looking emails, [to] trick companies into handing over data,” pompompurin said. “This would’ve never been found by anyone who would responsibly disclose, due to the notice the feds have on their website.”
US government must remedy poor cyber hygiene
The incident is a reminder that cyber hygiene across the US government remains poor. A report released by the US senate’s Committee on Homeland Security and Governmental Affairs in August highlighted cyber defence deficiencies across key departments, and says there has been little progress since an equally damning audit carried out in 2019.
“In 2019 the Subcommittee reported the failures of eight federal agencies to comply with basic cybersecurity standards,” the report says. “Two years later, seven agencies still fail at effectively securing data,” with only the Department for Homeland Security having significantly improved.
President Biden has been vocal in his plans to tackle cybercriminals, issuing an executive order in May and holding a cybersecurity summit in August following a spate of high-profile attacks. But insufficient training within the US government is a major hindrance to improving cybersecurity with the public sector, argues Chris Hauk, consumer privacy champion at online cybersecurity guide Pixel Privacy. “Hopefully, President Biden’s ‘Build Back Better’ plan will include actual improvements in cybersecurity,” says Hauk. “However, I have my doubts.”
He says previous government cybersecurity programs have been led by staff without sufficient expertise to deliver them, and adds: “Most federal programs include an incredible amount of waste, meaning nothing much will be done about cybersecurity by the time the last dollar of the plan is spent.”
Home page image by Domoyega/iStock






