
Attack automation, “spray and pray” techniques, and a shorter cyber killchain are some of the cyber attack trends posing an ever greater security threat to organisations, according to a new report from Houston-headquartered Alert Logic.
The privately held cybersecurity company took into account 1 billion security anomalies, millions of security events, and over a quarter million verified security incidents from April 2017 June 2018 to prepare the Critical Watch Report 2018.
Alert Logic said their research demonstrated a “significant uptick” in the trend of automated attacks, known as spray and pray, that roll through a set of IP addresses seeking vulnerabilities.
‘Innovation’ in New Attack Automation
While the targeting of IP addresses is not new, the use of automation is, as is the scale at which it is being utilised. Increasingly innovative automation techniques are also now being deployed, the firm said, examples of which it previously detailed in a blog post.
“So called spray and pray attackers are assaulting organisations at an unprecedented rate,” Alert Logic said. “The random nature of attacks has created a threat environment that is so aggressive, if there is proof-of-concept (POC) code out there, and your organisation is vulnerable, you will be attacked.”
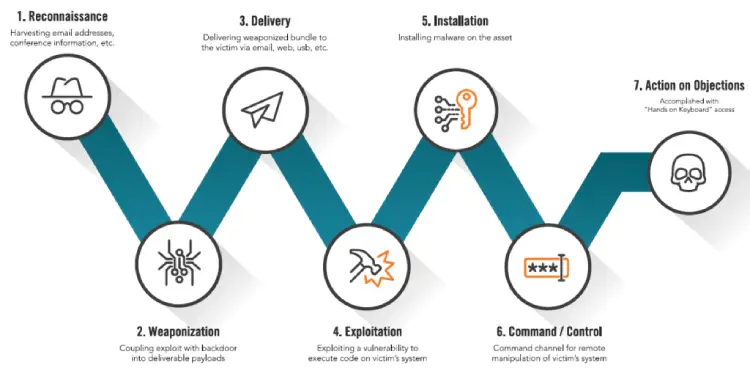
Alert Logic also used the report to highlight how the cyber killchain, or the structure and progress of an attack, is being shortened. Attack stages are now merging, Attack Logic said, giving organisations less of a chance to respond before they are affected and rendering standard methods of detecting and interrupting an attack ineffective.
The report outlined the traditional seven phases of the cyber killchain as reconnaissance, or harvesting information; weaponisation, coupling exploit with backdoor into deliverable payloads; delivery of the threat to the victim; exploiting the vulnerability to execute code the victim’s system; installing malware; command channel for remote manipulation; and action on objections, accomplished with hands on keyboard access.
“What we have observed in our new research is that attackers have modified this traditional killchain, effectively collapsing the first five phases into a single action, greatly speeding the process of identifying system vulnerabilities and launching a targeted attack,” the report says.
This merging of the five stages and the approach to leverage pre-defined and weaponised attack packages marks the most significant change in the cyber killchain since it was defined, Alert Logic said. The firm said it saw this technique used in 88 percent of cases.
“It’s no secret that attackers push the envelope and innovate attacks to abuse weaknesses anywhere they find them—in cloud and hybrid deployments, containerized environments, and on-premises systems,” said Rohit Dhamankar at Alert Logic.
“What is troublesome is the use of force-multipliers like automation to scale attacks for increased financial gain. This report demonstrates that attackers are gaining increasing sophistication in their ability to weaponize trusted techniques to exploit common vulnerabilities and misconfigurations for purposes such as cryptomining.”
Cryptojacking ‘Rampant’
Alert Logic also called cyptojacking “rampant”, with the report saying 88 percent of recent WebLogic attacks were cryptojacking attempts.
Alert Logic also said that the increased access and variety of hacking tools such as these mean that relatively small organisations no longer have a safety net. Greater use of cloud-based resources and more systems and applications that are accessible over the internet mean organisations with fewer customers and more limited use of sensitive data were at a lower threat risk.

App attacks are now the dominant attack method for multiple industry verticals, accounting for more than three quarters of attacks in information technology and services, media communication and entertainment, not-for-profits, and retail and hospitality.
“Most organisations can improve their security posture dramatically by focusing on the basics,” the report concludes. “To effectively improve security, organisations must embrace security hygiene, including proactive steps like patching, monitoring, and threat hunting.
“You can’t improve what you can’t see; understanding your assets, liabilities, and gaps is essential.”
IT security company Malwarebytes revealed in a report last month that that an organisation in the United Kingdom with 2,500 employees should expect to pay more than £821,000 per year in cybersecurity-related costs.






