
February’s “Patch Tuesday” set of software vulnerability fixes was a huge one, spanning 99 CVEs from Microsoft, 42 CVEs from Adobe and 6 from Intel, including a high priority – with a CVSS score of 8.2 – firmware update to patch (arguably ironically) the chip maker’s own Converged Security and Management Engine (CSME) subsystem.
Security teams wondering what to prioritise on the MSFT side could do worse than refer to the chart below from Trend Micro, which details the 12 critical CVEs from Microsoft, and four important bugs for which proof-of-concepts exploits are already public (meaning they are much more likely to be weaponised by cybercriminals.)
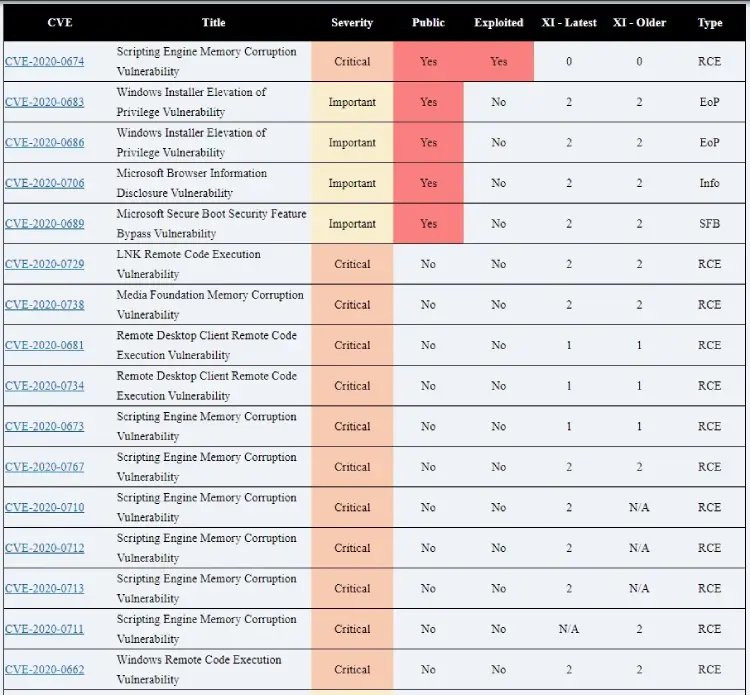
Adobe’s February patches meanwhile address 35 critical vulnerabilities: 12 for Acrobat Reader alone, spanning privilege escalation and use after free vulnerabilities.
As Automox‘s Jay Goodman puts it: “These vulnerabilities together can allow attackers to run arbitrary code or even full remote code execution with escalated privileges. Once the attacker is on a compromised host, they could use the privilege escalation exploit in Adobe Acrobat to elevate their privileges to Admin or System.
“Once there, the attack can essentially do whatever they wanted, including stopping AV, traversing the network or spreading to additional devices.
See also: Oracle Vulnerability Gives Hackers “Untraceable” License to Print Money
He added: “Adobe Acrobat Reader is one of the most pervasive applications on the planet with representation in every industry vertical. Estimates place Acrobat Reader at between 40 and 70 percent of all devices. When a vulnerability is discovered in applications that even your parents know by name, you know it is widespread.
For Microsoft, CVE-2020-0618 and CVE-2020-0662 stand out as remote code execution (RCE) vulnerabilities on Microsoft SQL Server Reporting Services impacting SQL Server 2012, 2014 and 2016 (32 and 64 bit) and Windows 7, 8.1, 10, Server 2008, 2012, 2016 and 2019, respectively. They would allow attackers to access a system and read or delete contents, make changes, or directly run code on the system.
Note also CVE-2020-0688 which is a SYSTEM-level RCE for Exchange using only a specially-crafted email. https://t.co/Fvn989b4ym
— Jake Codes (@codejake) February 11, 2020
Craig Young, computer security researcher for Tripwire’s vulnerability and exposure research team (VERT) added: “Anyone still managing their own Exchange servers will [also] want to pay careful attention to CVE-2020-0688.
“This bug allows remote attackers to take complete control of an affected mail server simply by sending a crafted email. What’s worse is that Microsoft has rated this as being more likely to be exploited in attacks. As far as I’m concerned, this is about as bad as it gets and deserves the immediate attention from affected organizations.”
Note MSFT’s Extended Support Releases…
Todd Schell, senior product manager, security, at Ivanti noted: “Another notable, we will call it discrepancy, this month is the extended support releases.
“Windows 7, Server 2008 and 2008 R2 ESU updates are still being documented publicly and are listed in the standard WSUS catalog. This is likely to cause some confusion. Does this mean everyone has access? No, you do need an ESU with Microsoft in order to meet the specific criteria for the free options that Microsoft has outlined in the Windows 7 ESU FAQ. Also of note, there is an ESU License Preparation Patch.
“There are four things you need to review on your ESU targets to ensure you will be able to patch without issue. You need to ensure the SHA-2 support updates are applied, that you meet Service Stack Update prerequisites, that you have pushed this new licensing preparation patch to the systems, and that you have your ESU license key in place.”
On the Adobe side, one still unanswered question: when do regular Magento patches start landing? Given the ecommerce platform’s regular mention in headlines for Magecart-style card scraping attacks, users will no-doubt hope so.
As Trend Micro’s Zero Day Initiative notes: “Adobe released a patch for their Magento Commerce platform in late January to correct six CVEs. Adobe acquired Magento last May for $1.68 billion USD, and this appears to be the first patch released for the platform since the acquisition. None of these Critical- and Important-rated bugs are listed as publicly known or under active attack. What isn’t clear is if patches for Magento will eventually be included in the regular Patch Tuesday.”
(Computer Business Review is pressing this point with Adobe…)






