
Some of the biggest beasts of the tech world have teamed up to launch a new Open Source Security Foundation (OpenSSF) — which will be hosted at the Linux Foundation and take over the work of the foundation’s Core Infrastructure Initiative (CII).
GitHub, Google, IBM, JPMC, Microsoft, NCC Group, OWASP Foundation, and Red Hat are all founding members. Their aim: safeguarding the security of some of the most widely used open source packages from upstream pollution by malicious actors.
The desert of the tech world is, of course, littered with such noble initiatives and the proof lies in the less glamorous pudding of providing committed resource to communities needing extra eyeballs, but the OpenSSF appears to recognise this, with what looks to be a clear-eyed focus on pragmatic solutions, even if some may appear unlikely at scale; i.e. Red Teaming to ensure malicious changes don’t pass code reviews.
They launched the project today as concerns grow about the ability of attackers to compromise open source codebases (some of which have small communities but are ubiquitous in production environments), with potentially wide-reaching consequences for organisations that are often unaware at an enterprise level of the extent to which OSS packages proliferate across their IT estates — even in many commercial tools.
As Microsoft CTO Mark Russinovich put it: “Open-source software is core to nearly every company’s technology strategy and securing it is an essential part of securing the supply chain for all, including our own. With the ubiquity of open source software, attackers are currently exploiting vulnerabilities across a wide range of critical services and infrastructure, including utilities, medical equipment, transportation, government systems, traditional software, cloud services, hardware, and IoT.”
10 Billion Downloads per Week of npm Packages Alone
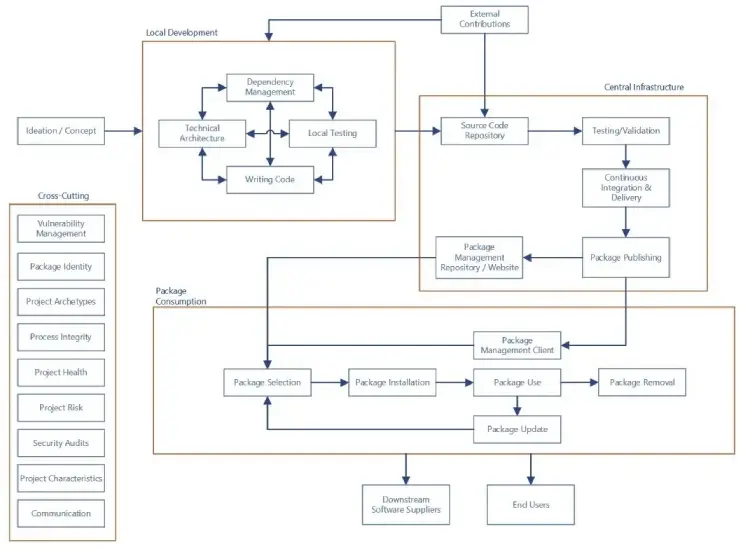
To put the potential risk in perspective, Sonatype’s fifth annual State of the Software Supply Chain Report suggested that UK enterprises alone downloaded over 21,000 software components with a known vulnerability in 2019. (The numbers for open source package downloads are huge: In 2018, download requests for Java components alone hit 146 billion; those of npm packages ran at 10 billion per week.)
Open source mailing lists meanwhile proliferate with the laments of security engineers trying to rouse upstream security contacts for open source projects, with decidedly mixed success. (Many bugs don’t get acknowledged for months, let alone patched).
The new foundation — which will be be supported by Linux Foundation membership dues, rather than grants like the CII — will focus on “metrics, tooling, best practices, developer identity validation and vulnerability disclosures best practices.”
Among its proposals: helping provide security professionals to conduct security reviews of high-risk open source projects; central curation of clear guidance on secure configuration; a push towards “on by default” static analysis of source code; analysis of regularly cut and pasted code snippets in Stack Overflow; bug bounty programmes with rewards for accepted patches; and expanding “secret detection” capabilities in GitHub, GitLab, NPM, PyPI et al. (Secrets management refers to ensuring that credentials/tokens/crypto keys are not inadvertantly disclosed by a programme).
In the future, there is a plan to focus resources on the most mission-critical software identified by Harvard’s Lab for Innovation Science in its major open source census, published in February this year. Microsoft said it wants to help create an open-source software ecosystem where the time to fix a vulnerability and deploy it “is measured in minutes, not months.” It’s a bold ambition. It also comes with what looks like a well thought through plan. Overstretched, underappreciated open source project maintainers will be wandering if the cavalry is arriving.
You can see the Top 20 most widely used Open Source packages here.






