
CEOs and CFOs are being targeted by a phishing campaign that uses a flaw in Microsoft’s Office 365 productivity suite, lets a hacker pose as the executive and send out fraudulent invoices and financial requests. This works regardless of whether multi-factor authentication (MFA) is enabled, businesses are warned.
This type of attack, known as a business email compromise (BEC) campaign is “widespread on the internet now and targeting large transactions of up to several million dollars each,” according to cybersecurity vendor Mitiga, which discovered the breach after being called in to investigate an incident at an unnamed company following reports of unusual email activity.
One real world example of this type of attack was detailed by Mitiga in a new report. The incident combined high-end spear-phishing with an adversary-in-the-middle (AiTM) attack and an exploit in Office 365 that allowed the hacker to bypass MFA.
The hackers start by sending a phishing email targeted to a senior executive that looks like a legitimate document from DocuSign. it contains a malicious link which redirects to a fake Microsoft Office 365 login page. Entering details sends the attacker the target’s username and password.
The attack also implements a proxy server between the client and the real Microsoft server that allows the hacker to bypass MFA, meaning they can intercept a valid session cookie and obtain persistent access to monitor the account and emails.
How to combat the Office 365 phishing scam
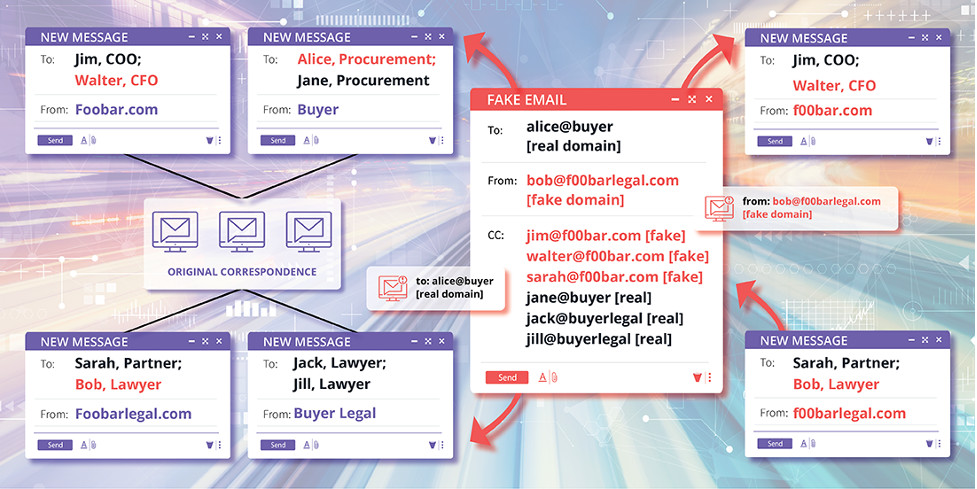
Once into the system and able to monitor email threads, the hacker can set up a fake domain very similar to that of the company and insert themselves into an existing email thread, usually one involving a financial transaction.
The hacker would find a message in the thread about payment details and reply, suggesting there is an issue with the payment system due to an ongoing audit that has led to the target bank account being frozen. The hacker then offers up alternative payment information in an attachment.
The case that sparked the investigation didn’t result in fraud due to the “quick action of the company involved”, Mitiga says, but the attacker was able to access sensitive information that could only be obtained by compromising a user in the organisation.
“The email that the attacker sent included all the recipients of the original thread,” explained Mitiga in a review of the incident. “However, the attacker created forged domains using similar domain names, such as using capital i to replace an l, and so on.” This was put in the ‘bcc’ email field so other recipients couldn’t see the domain.
After containing the threat, Mitiga found that the hacker spent time roaming around the Office 365 environment, including accessing emails through outlook and files through Sharepoint to identify the best target email thread.
Mitiga says account security should be tied to specific authorised computers and phones to prevent criminals compromising cloud application accounts from a different location. They also recommend still using multi-factor authentication as it is a vital tool for protecting users from cyber attacks but to take additional steps to check the authenticity of domains.
Tech Monitor is hosting a roundtable in association with Intel vPro on how to integrate security into operations. For more information, visit NSMG.live.
Read more: Vulnerability leaves Office 365 cloud data open to attack
Homepage image of Office 365 courtesy of abalcazar/iStock






