
Microsoft’s Detection and Response Team (DART) said it discovered six threat actors in the network of a “large, multinational company”, after being called in to deal with one apparent intrusion by an unnamed attacker.
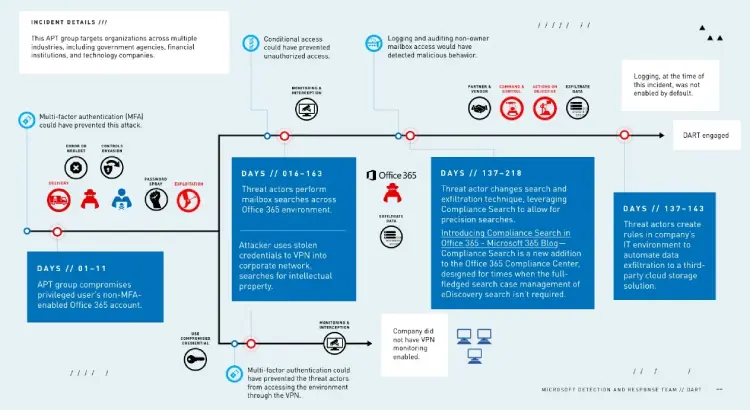
DART said it has been contracted to deal with a “sophisticated, state-sponsored advanced persistent threat” (APT) that had hacked the company and persisted in its network for eight months despite efforts to remove it.
That initial attack had involved use of a “a password spray attack to gain the company’s Office 365 administrator credentials”.
See also: Aussie Security Firm Brute-Forces Kaspersky’s Encryption to Reveal ASUS Hack Targets
(Password spray attacks involve trying a range of common passwords, e.g. “password”, “qwerty”, to gain initial access to an account.)
DART said in a recent case study: “[The APT] used the stolen credentials to conduct multiple mailbox searches for other credentials that were, unfortunately, often shared via emails without digital rights management between the company and its customers.
“The attacker specifically searched for these emails in certain regions and market segments… this attack was most likely a case of cyberespionage as the attacker was looking for specific information—in this case IP in certain markets.”
See also: 10 Major Global Telcos “Completely Penetrated” by Chinese APT
In an uncommon move, the attacker used the customer’s existing systems, including eDiscovery, the Compliance Search feature, and Microsoft Flow, to automate stealing its search results, the response team noted.
By “living off the land” and easing its workload, the attacker found ways to turn on existing features that the customer had implemented but was not actively using or had not turned on, it noted in the report: “These systems had not been configured to gather logs from high-value systems or to detect unauthorized use of them.”
Five More APTs in the House
Strikingly, DART said it also identified five “additional, distinct attacker campaigns persisting in the environment” that were unrelated to the initial incident.
It did not name any of the APTs or attribute the attacks.
Without further detail it is impossible to fully confirm the incident — security practitioners are incentivised to emphasise their ability to identify attacks/security incidents where others failed (owing to supposed superior technique, better tools, etc.) but incident response specialists tell Computer Business Review that finding multiple APTs in a network is not entirely uncommon.
DART emphasised the importance of using multi-factor authentication (MFA), conditional access, and enabling logging as part of routine deployment plans, as well as disallowing legacy authentications that don’t allow MFA. (i.e. Older Microsoft Office apps, and apps using mail protocols like POP, IMAP, and SMTP).
It also emphasises the importance of good quality logs, i.e. via a Security Information and Event Management (SIEM) tool, to help assist in identifying attacks.






