
A new malware as a service (MaaS) loader has been discovered in action. The loader, named Buer and detailed in a new report from threat researcher Sophos, reveals the growing sophistication of ready-made malware that developers sell to cybercriminals targeting businesses and governments.
The Covid-19 pandemic has triggered a rapid increase in cybersecurity breaches in 2020. This week the National Cyber Security Centre revealed it had thwarted a record 723 serious threats on UK state institutions so far this year, a pattern of increased cybercriminal activity that has been mirrored around the world.
This boom in cyber threats can be attributed in part to the rise of MaaS offerings, which make it easier than ever for non-expert criminals to exploit the latest security vulnerabilities.
The definition of malware as a service
As the name suggests, malware as a service involves developers of malware selling their work to clients who want to launch cyber attacks but lack the technical skills to do so.
“MaaS solutions have become increasingly popular for the exact same reason that software as a service (SaaS) solutions have become increasingly popular: they lower the barriers to entry in terms of both costs and necessary expertise,” says Brett Callow, threat analyst at Emsisoft.
“Thanks to MaaS, anybody can become a cybercriminal, even those with relatively low technical expertise. MaaS and the associated underground economy have undoubtedly helped shape the threat landscape. Attacks that would once have required a particular skillset are now available to one and all, resulting in an overall increase in sophistication.”
Sean Gallagher, senior threat researcher at Sophos, recently published a paper on the Buer Loader, a new type of MaaS which allows hackers who purchase it to infiltrate networks and was used to launch a Ryuk ransomware attack in September. He says: “You could buy Buer Loader to download Ryuk, and if you have a web server and know how to do some basic things with Windows and Linux on the back end, you can pretty easily get into a network, no experience required.”
What are the different types of malware as a service?
Malware as a service comes in many guises, depending on a user’s objectives and the kind of system, organisation or individual they wish to target.
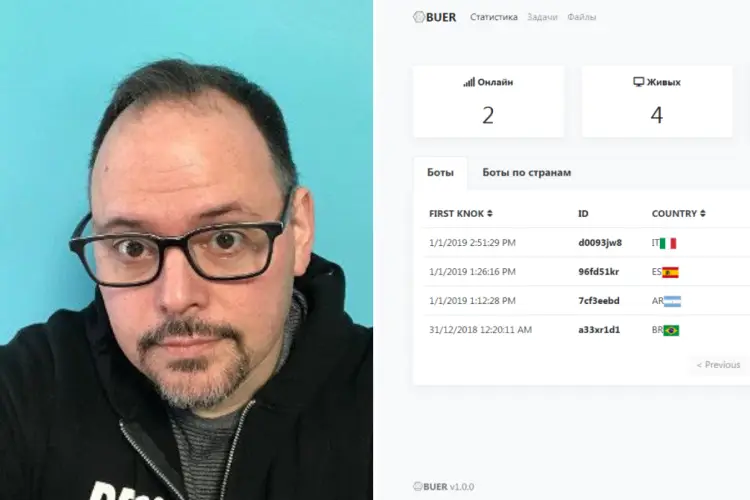
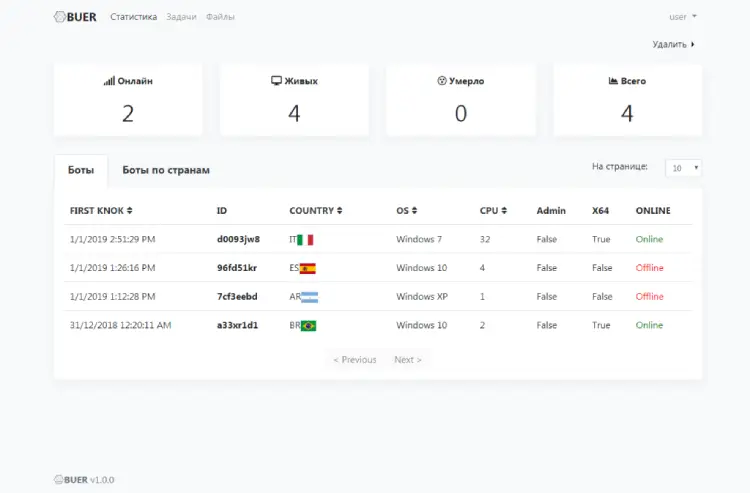
- Customised malware: Buer is an example of one common form of MaaS, in which the seller customises a malware attack to the buyer’s needs and provides a dashboard that allows them to track its progress. “Buer is set up so that you pay a fee and the developers will build a version of the malware for you that attaches specifically to the command and control service they give you,” explains Gallagher.The client then gets access to a control panel that would be familiar to anyone who runs a SaaS system, showing information about where the malware’s bots have landed, sorting them into different categories such as the processing power of the infected computer and its location and operating system. “You get this custom-built backend that allows you to control all of the malware you send out and track where all the downloads go,” Sean explains. This can be a low-cost solution for criminals, with Sophos reporting that access to the Buer Loader starts from just $350.
- Rent a bot farm: Enterprising hackers have also been known to rent out access to their existing networks of compromised machines. “We’ve seen that in the past where people will rent out computers infected with some sort of malware to allow other things to happen, like to send out spam or to distribute other malware on the networks,” Gallagher says.
- Ransomware as a service: Another common form is ransomware as a service, in which ransomware developers sell access to their encryption software, their code, and the back-end that controls it, to smaller cybercriminal operations. Gallagher says: “They go out and act as sort of affiliates and install it on people’s networks and then they collect a cut [of the ransom] for having done the installation.”
Examples of malware as a service – Emotet, Buer and more
The most commonly used malware as a service platform is Emotet. It is usually deployed to launch ransomware attacks or to send secondary MaaS loaders, such as TrickBot and QakBot, into infected networks where they can unleash their payloads.
Hackers have been increasingly using spam email to try and distribute Emotet during the Covid-19 pandemic, with HP reporting that the number of Emotet spam campaigns it analysed in the last quarter rose 1,200% compared to Q2. Though HP declined to put a precise figure on the number of campaigns it probed, a spokesman told Tech Monitor it isolated thousands of Emotet samples.
However, Gallagher believes Emotet is on its way out, with the number of instances of use declining, and says new kid on the block Buer could be set to take its place as MaaS of choice.
He says: “[Buer] has taken a while to gain traction with the user base, but they’ve been talking about it for the last 16 months or so.
“We first encountered it directly as part of a Ryuk attack we responded to in September – it was being used by attackers to try and get into one of many companies being targeted by spear phishing attacks.
“Buer is being positioned to replace Emotet, which we’ve seen dropping down over recent months.”
Malware as a service and Covid-19
Spear phishing attacks, in which emails purporting to be from a trusted source are used to con victims into downloading malware, have become commonplace during the Covid-19 pandemic. Gallagher says this tactic was used to distribute the Buer Loader in the Ryuk attack his team discovered.
“People got an email saying ’I’m an outsourcing expert and am taking money out of your payroll, and this document explains why,” he says. “When they clicked the link it actually downloaded a malicious document from a Google Drive account that in turn loaded Buer.”
How to stop malware as a service
Though there is no magic formula for stopping malware as a service breaches, Gallagher says there are simple steps organisations can take to protect themselves.
“You really need good defence in depth in place,” he says. “The other big thing is teaching people not to click on links. If you can stop them clicking you cut out about 80% of your problems.”
He added that for remote teams a lot of issues arise from not having protected VPNs in place.
“We saw a big jump in remote desktop protocol access early on during the lockdown – one of the major ways that ransomware attackers in particular get in is by busting in through a remote desktop protocol,” he says. “If you don’t have adequate protections it makes it that much easier for them.”
The cost and impact on businesses and Governments
With the average cost of a data breach in 2020 coming in at $3.8m, according to a report carried out by IBM and the Ponemon Institute, the potential rewards for malware as a service vendors are high, and the risks to businesses considerable.
Alex Holland, senior malware analyst at HP, says he expects to see a pattern of weekly Emotet spam runs to continue into 2021 as cyber attackers try to infiltrate businesses by bombarding employees with bogus emails.
“The targeting of enterprises is consistent with the objectives of Emotet’s operators, many of whom are keen to broker access to compromised systems to ransomware actors,” he says.
Emsisoft’s Callow says that while MaaS is generally associated with unskilled attackers, it is increasingly being deployed by advanced cybercrime groups and even nation states.
“A number of ransomware groups – including the operators of Ryuk and Conti – have used the Trickbot MaaS platform as an easy way to reach, and encrypt, already compromised systems,” he says.
“Similarly, North Korea’s Lazarus Group and other advanced persistent threats (APTs) have been observed to leverage Trickbot’s solutions. This represented a marked shift – nation-backed APTs did not previously use off-the-shelf products from for-profit criminals – and provides an indication of how advanced and effective MaaS solutions have become.”






